Identity & Accounts
Whoooooo are you? Who, who, who, who?
Identities and Accounts enable your app to recognize the person using it and taylor the interface and experience to that individual. However this can be difficult to implement securely. This post will show you how to use BC to handle Indentity and Accounts so you don't need to invest the time and energy yourself and can instead focus on the core value of your app.
BC
BC is a Universal Blockchain Library which this post will use to provide Identity and Accounts inside a Fyne app.
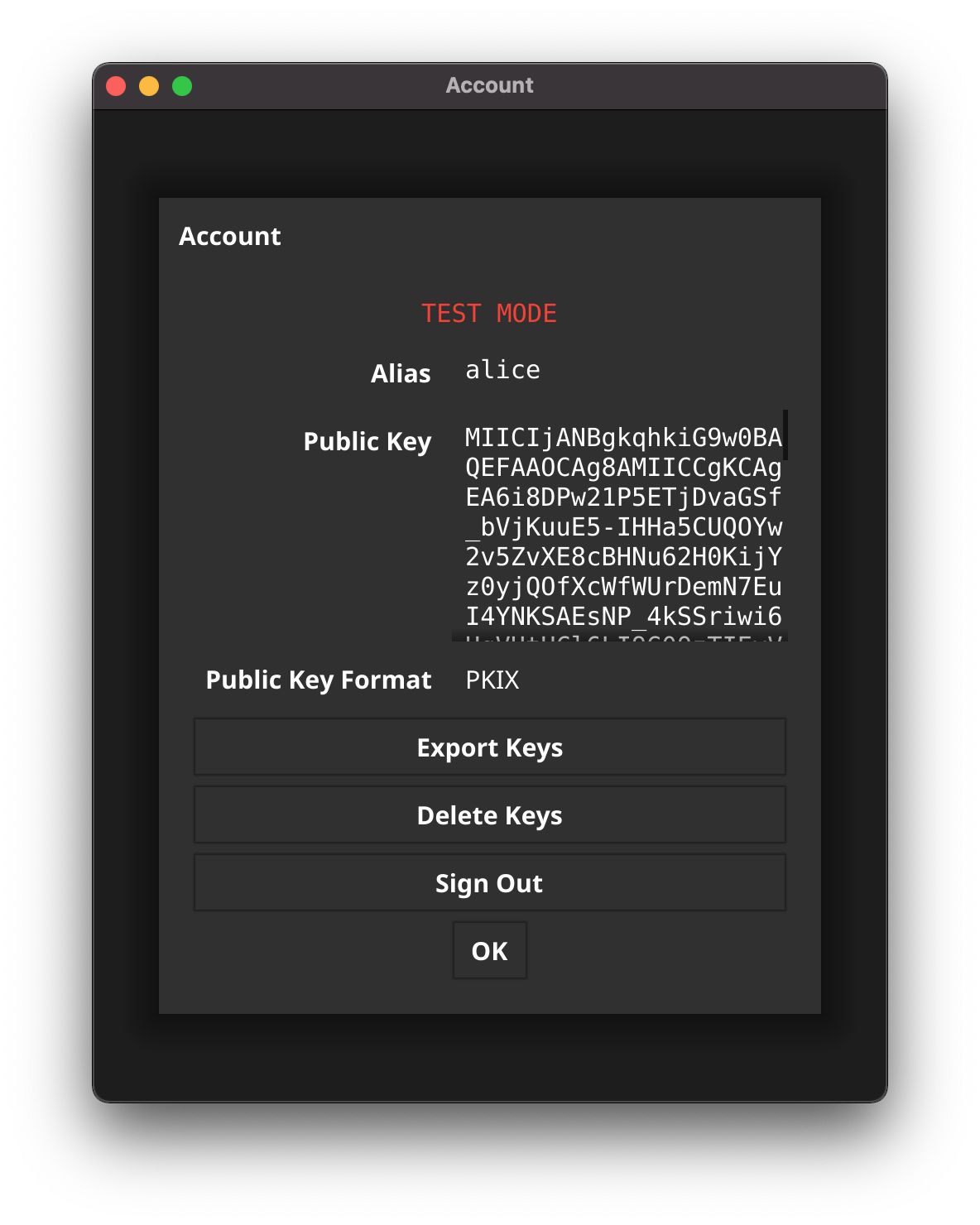
In BC an Identity is a pair of Alias and Public Key that uniquely represents a user. An Account is an extension of an Identity that includes a Private Key; think of an Account as a signed-in Identity.
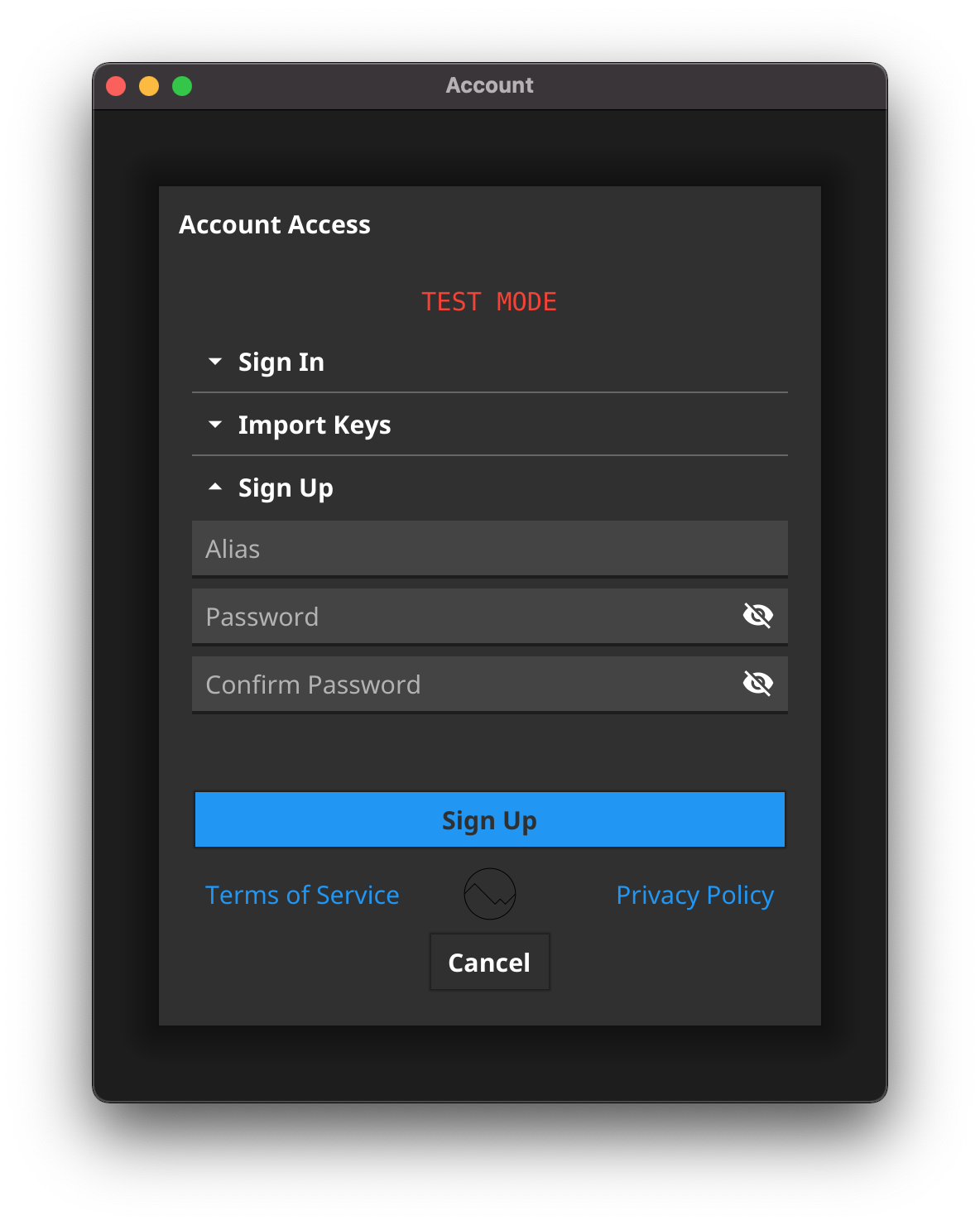
Sign Up
When your users sign up they choose their own Alias and Password, then BC generates an RSA 4096bit Asymetric Keypair. The Alias and Public Key are registered when they are mined into the Alias blockchain. While the Private Key is encrypted with the Password and stored exclusively on their device.
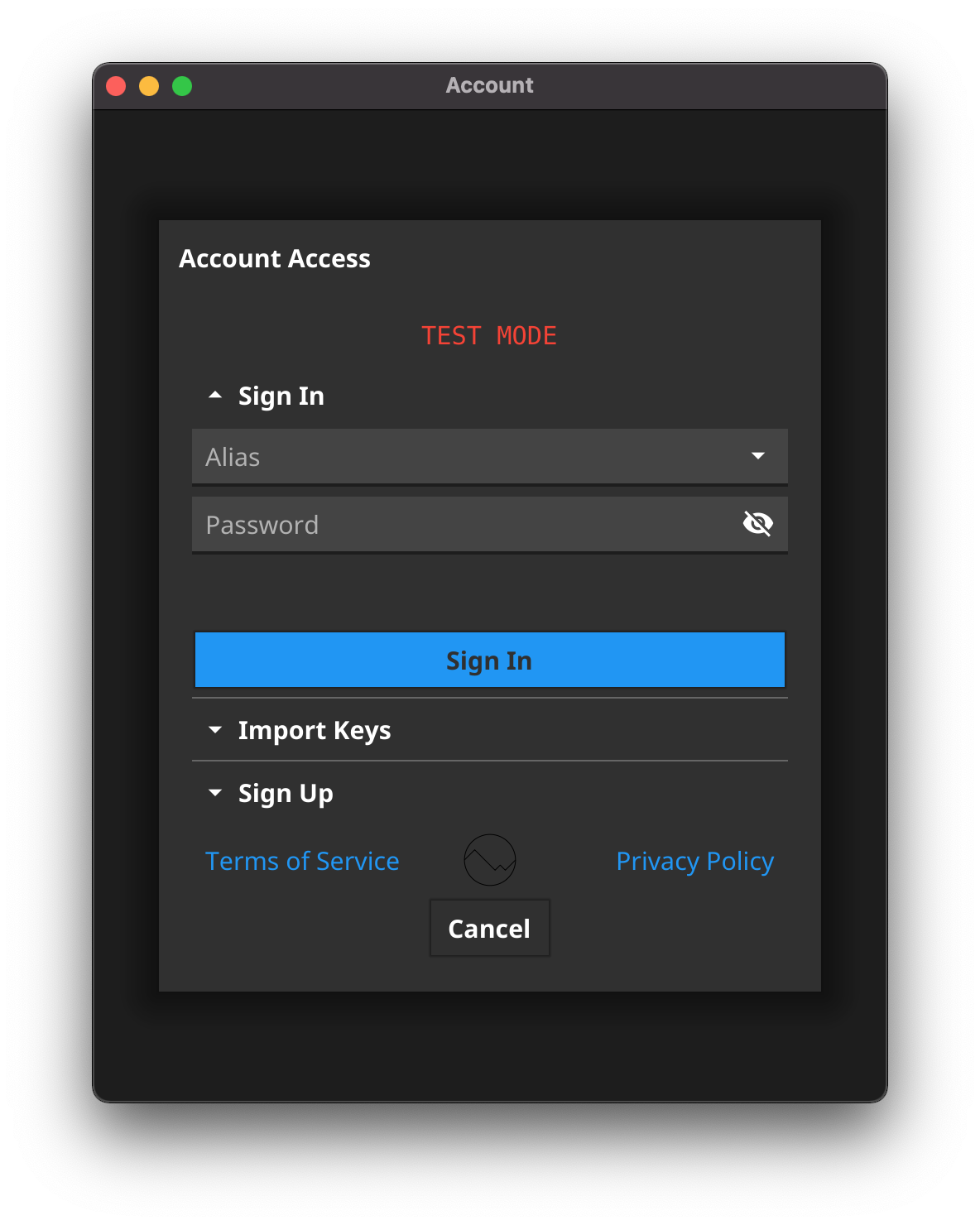
Sign In
A user can sign in by entering their Alias and Password at which point their Private Key is loaded from their device, decrypted, and made available for Cryptographic Operations (see below).
Import/Export
BC provides a mechanism for account holders to Export their Private Key from one device and Import it into another device. Enabling their account to follow them from device to device

Cryptographic Operations
Once an account is signed in, it can be used to perform common cryptographic operations such as Encrypting, Decrypting, Signing, and Verifying.
Encrypting & Decrypting
If your app transmits or persists sensitive information then you should protect it with encryption. Asymetric Encryption (like RSA 4096bit) offers high security for small pieces of data, but when working with large datasets it is best to use Symmetric Encryption (like AES 256bit) for the dataset itself, and then encrypt the Symmetric Key with the Asymetric Key.
Signing & Verifying
Cryptographic Signatures can ensure that data has not been corrupted, or tampered with.
Test vs Live Mode
By default apps will be in TEST MODE which runs on a network intended for testing purposes. Once you're ready to distribute your app to real-world customers, use the fyne release, or go build -tags release commands to configure your app to be in LIVE MODE.
If you have any questions, or encounter any issues get in contact.